Link a OneLogin Application to Marigold Engage by Sailthru
This guide walks you through configuring a OneLogin application to enable SAML-based Single Sign-On from OneLogin for Marigold Engage by Sailthru. In this scenario, the OneLogin application is the SAML Identity Provider.
- In OneLogin click “Administration” and then select “Applications” from the “Applications” menu:
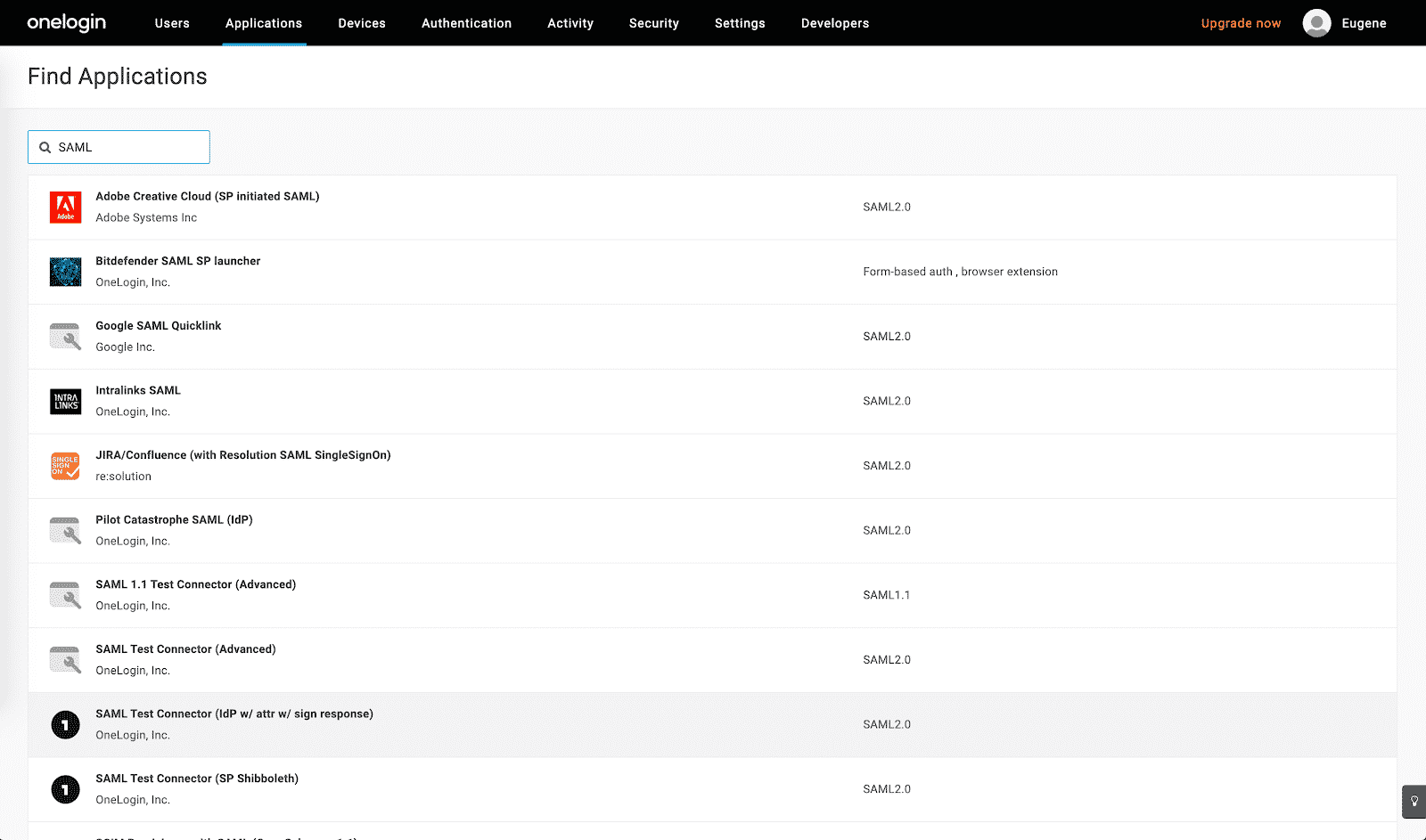
- Click “Add App” and search for “SAML”. Select “SAML Test Connector (IdP w/ attr w/ sign response)”:
- Change the “Display Name” of the app and toggle off the slider “Visible in portal”:
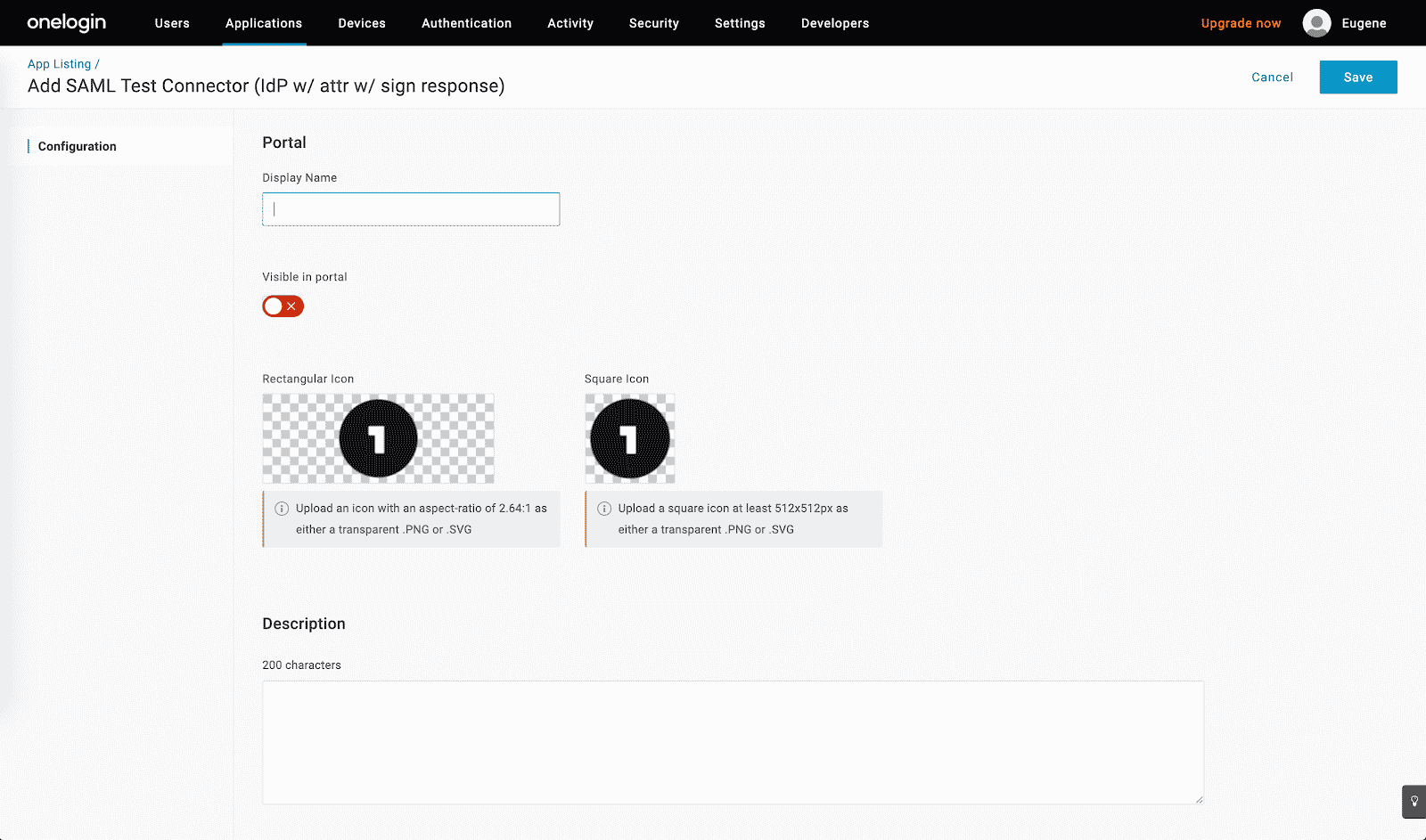
- Click Save.
Configure your new OneLogin application
- Decide the name of the SAML connection that will be used by Marigold Engage by Sailthru. This should be in the format of
saml-<companyname>, e.g.saml-sailthru. In the following steps, you’ll insert this name in place ofSAML_CONNECTION_NAME. - Open the “Configuration” tab:
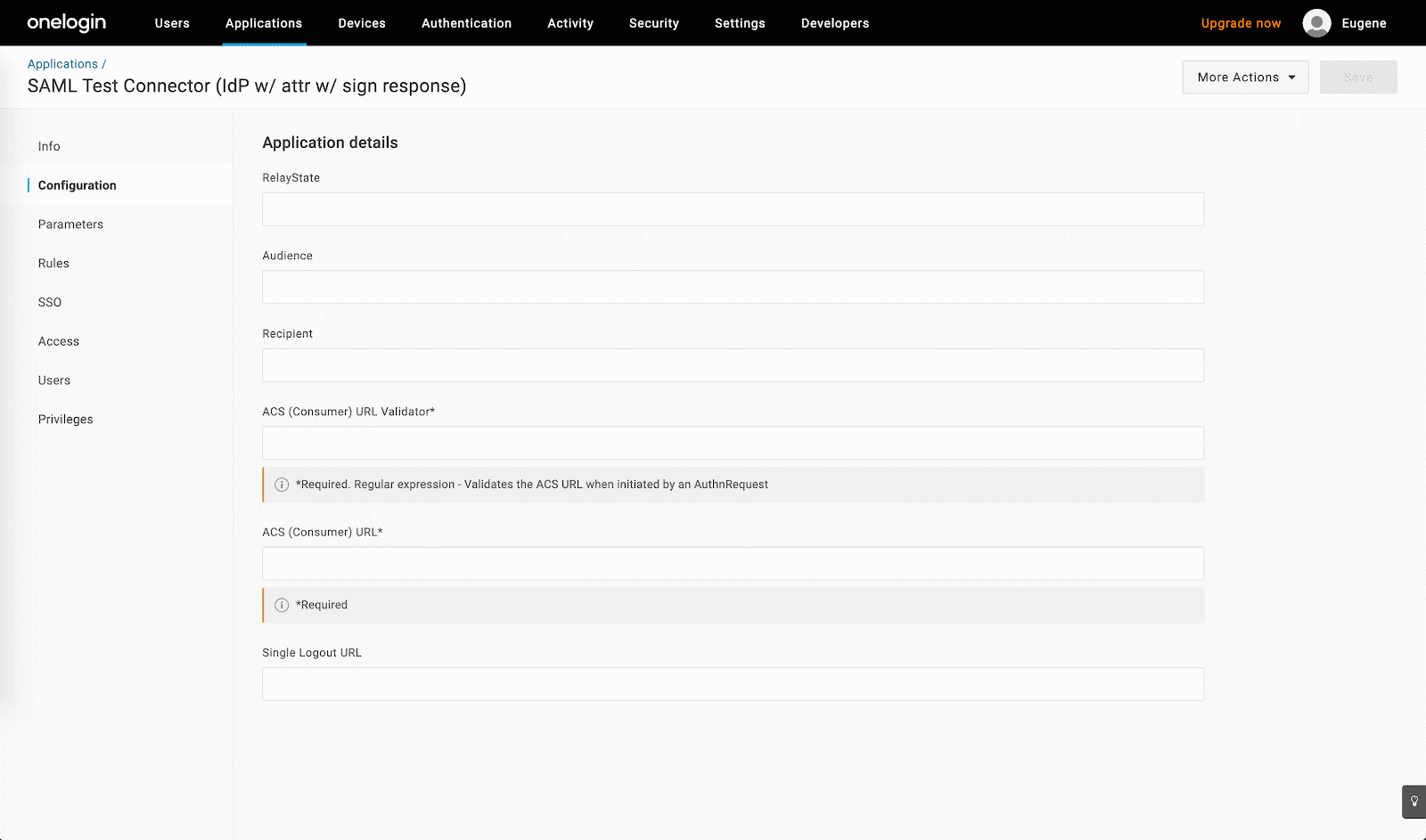
- Enter the following settings:
urn:auth0:sailthru:SAML_CONNECTION_NAMEas the value for the “Audience” field[-a-zA-Z0-9@:%.+~#=]{2,256}.[a-z]{2,6}\b([-a-zA-Z0-9@:%+.~#?&//=]*)as the value for the “ACS (Consumer) URL Validator” fieldhttps://login.sailthru.com/login/callback?connection=SAML_CONNECTION_NAMEas the value for the “ACS (Consumer) URL” field
- Go to the “Parameters” tab:
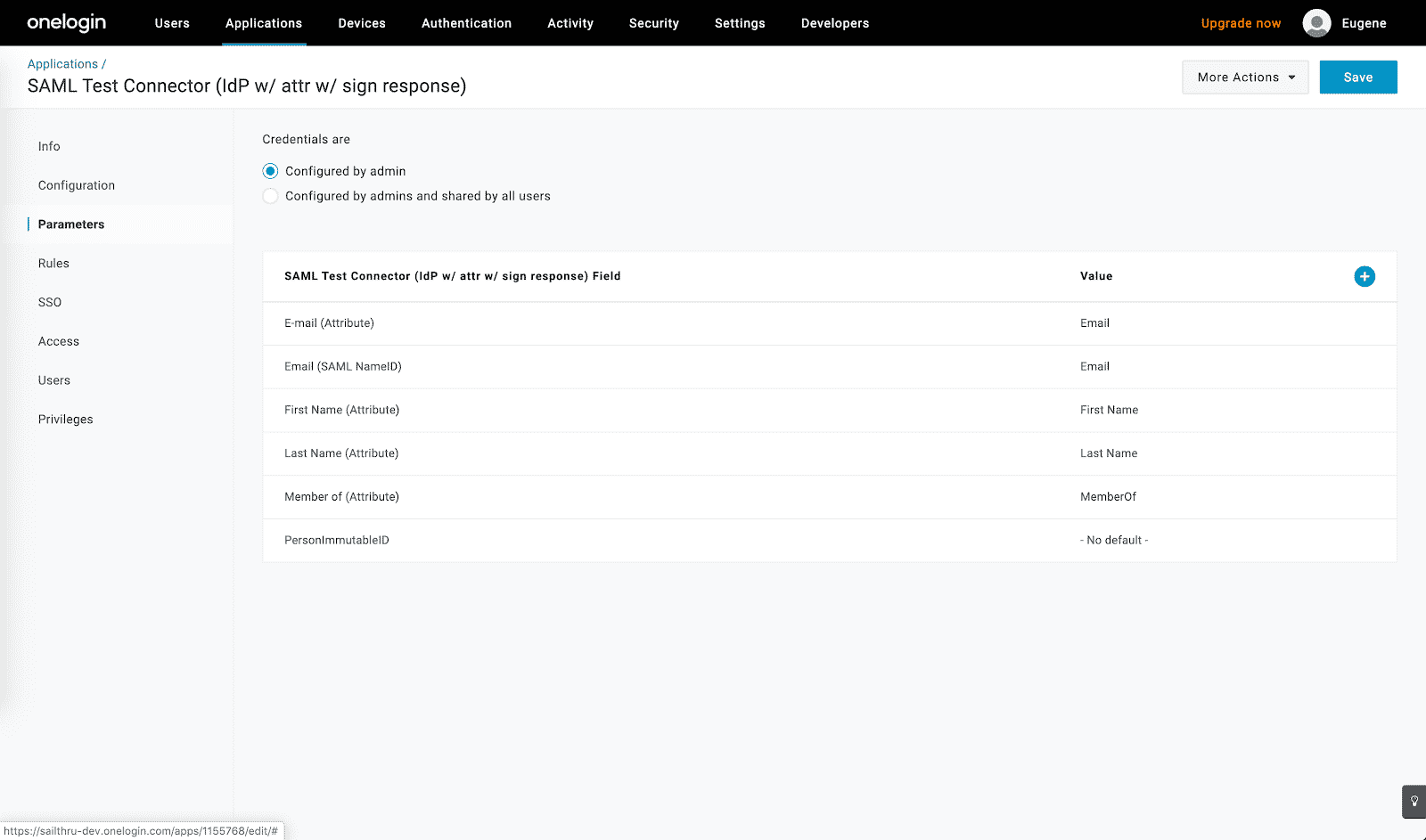
- Make sure that the user’s email address is specified as the SAML NameID attribute:
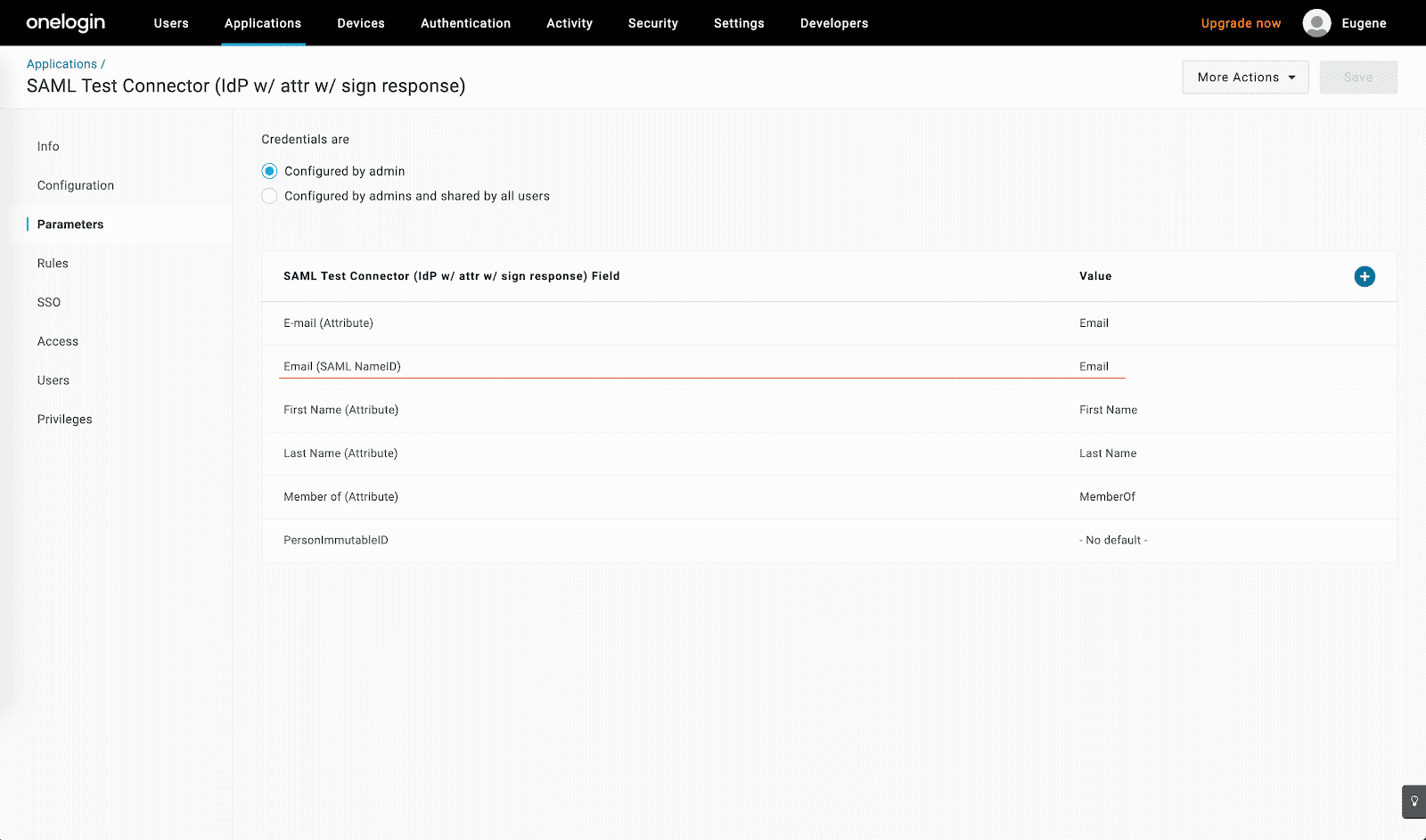 Remember the email address sent from OneLogin must match the email address associated with the user within the Marigold Engage by Sailthru platform.
Remember the email address sent from OneLogin must match the email address associated with the user within the Marigold Engage by Sailthru platform. - Click the Plus icon and add
http://schemas.xmlsoap.org/ws/2005/05/identity/claims/givennameSAML attribute: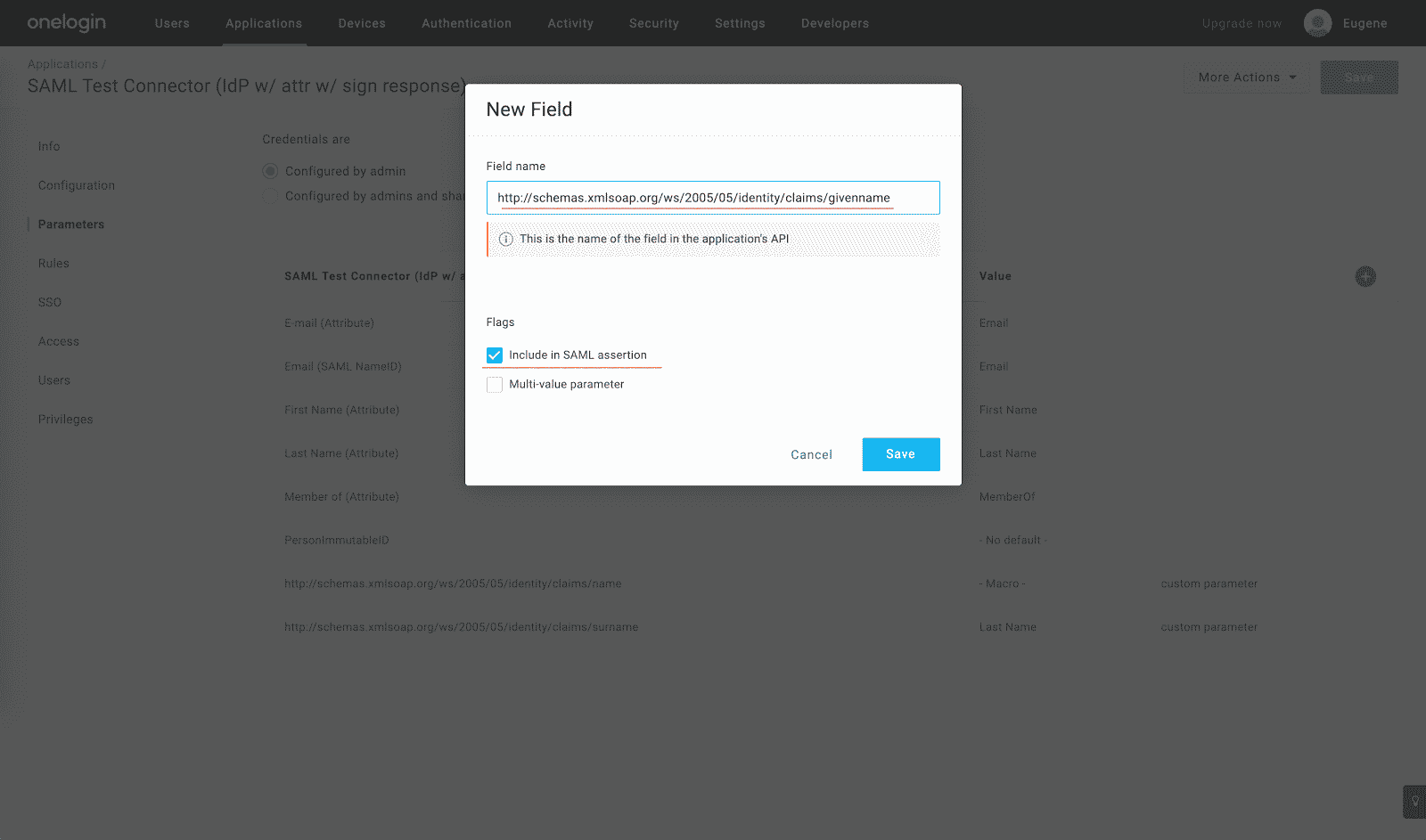
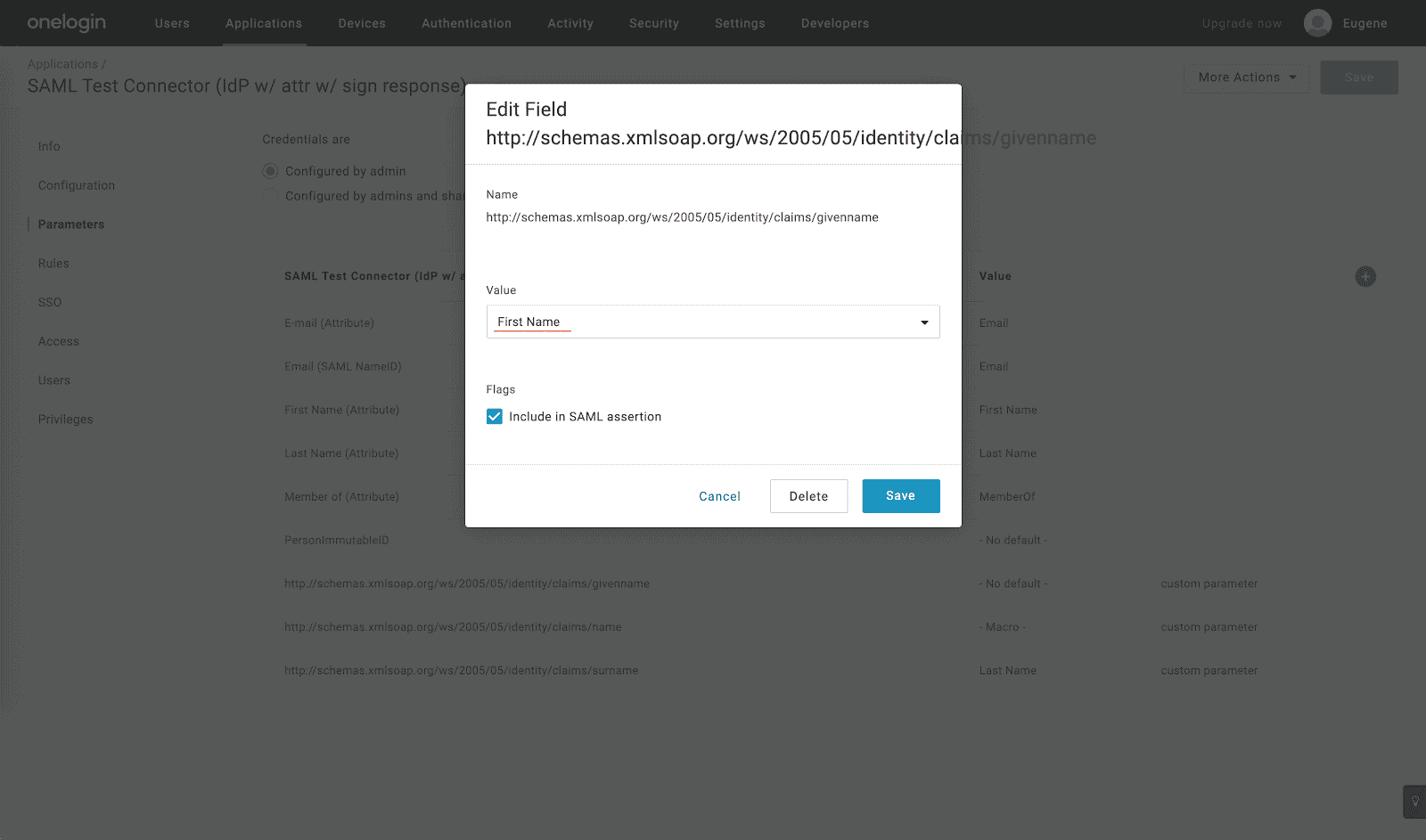
- Click the Plus icon and add http://schemas.xmlsoap.org/ws/2005/05/identity/claims/surname SAML attribute:
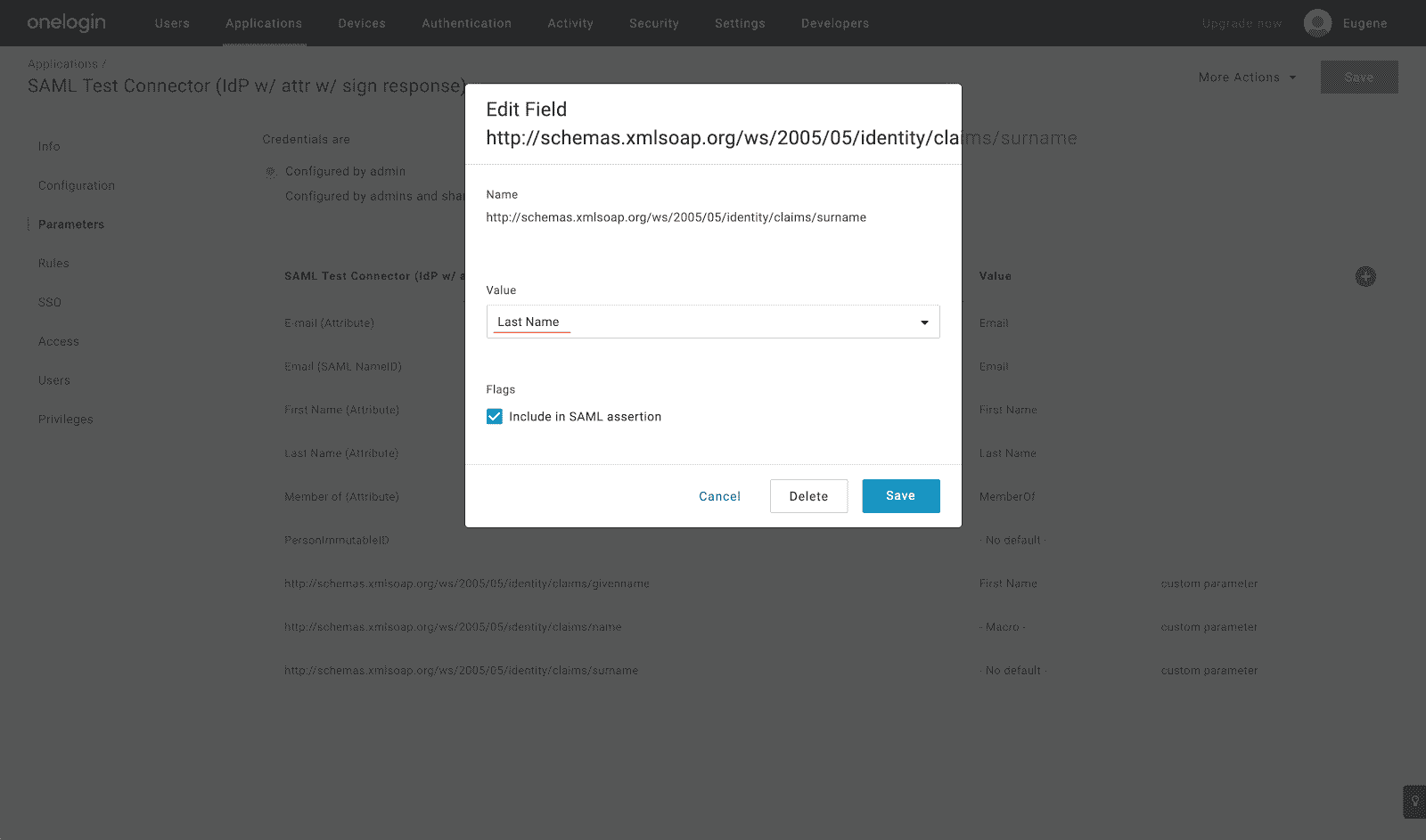
- Click the Plus icon and add
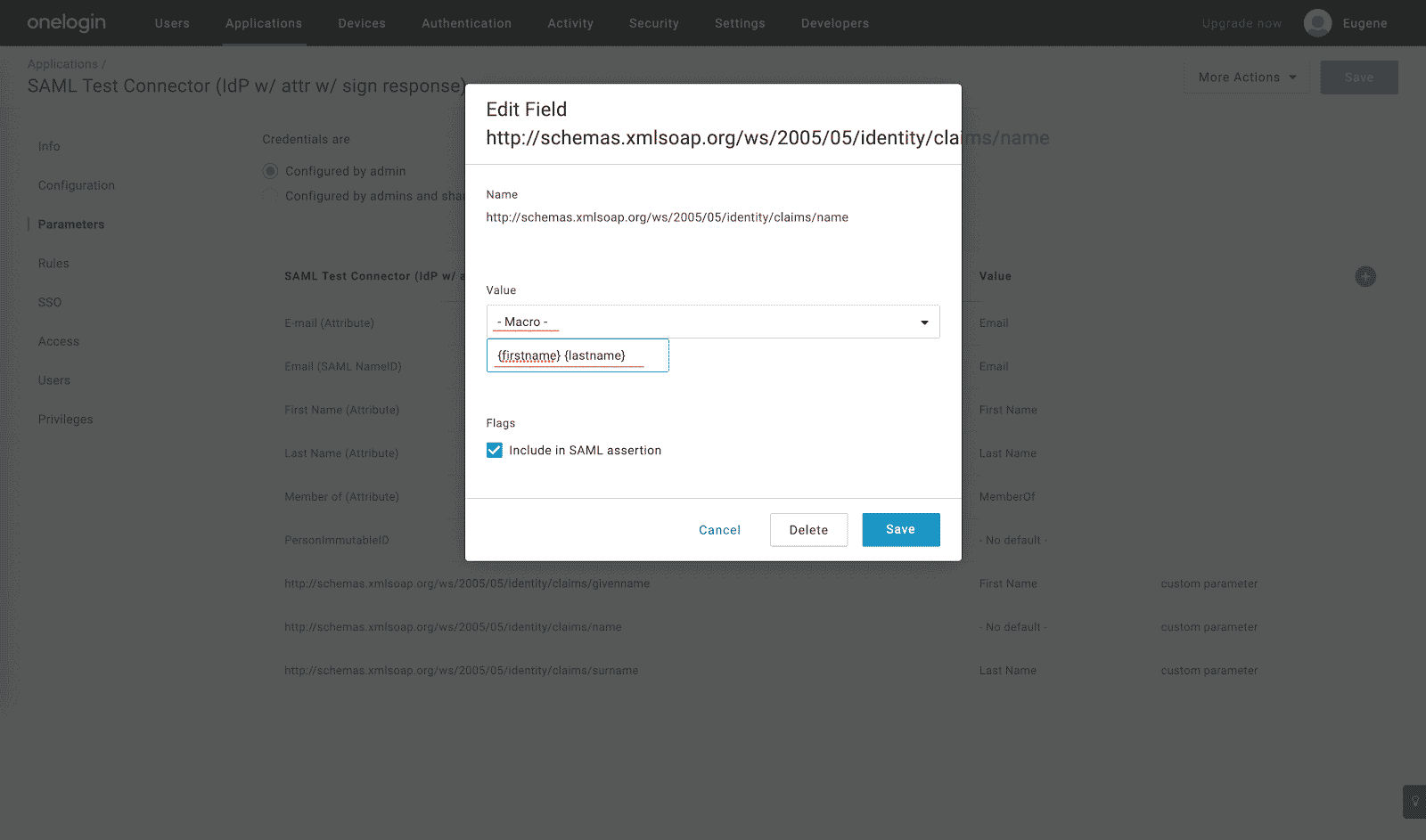
http://schemas.xmlsoap.org/ws/2005/05/identity/claims/nameSAML attribute as a macro field with the{firstname} {lastname}value: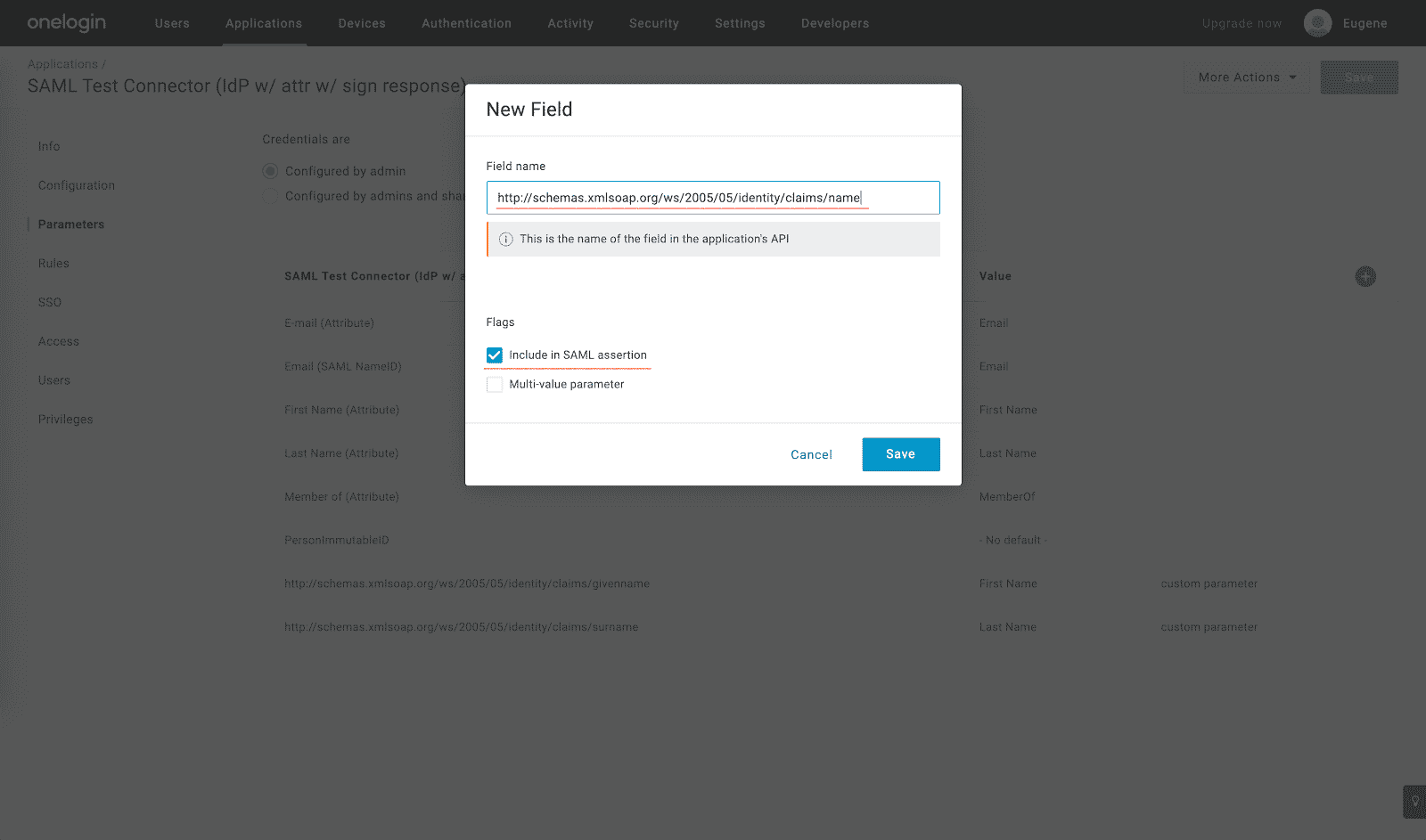
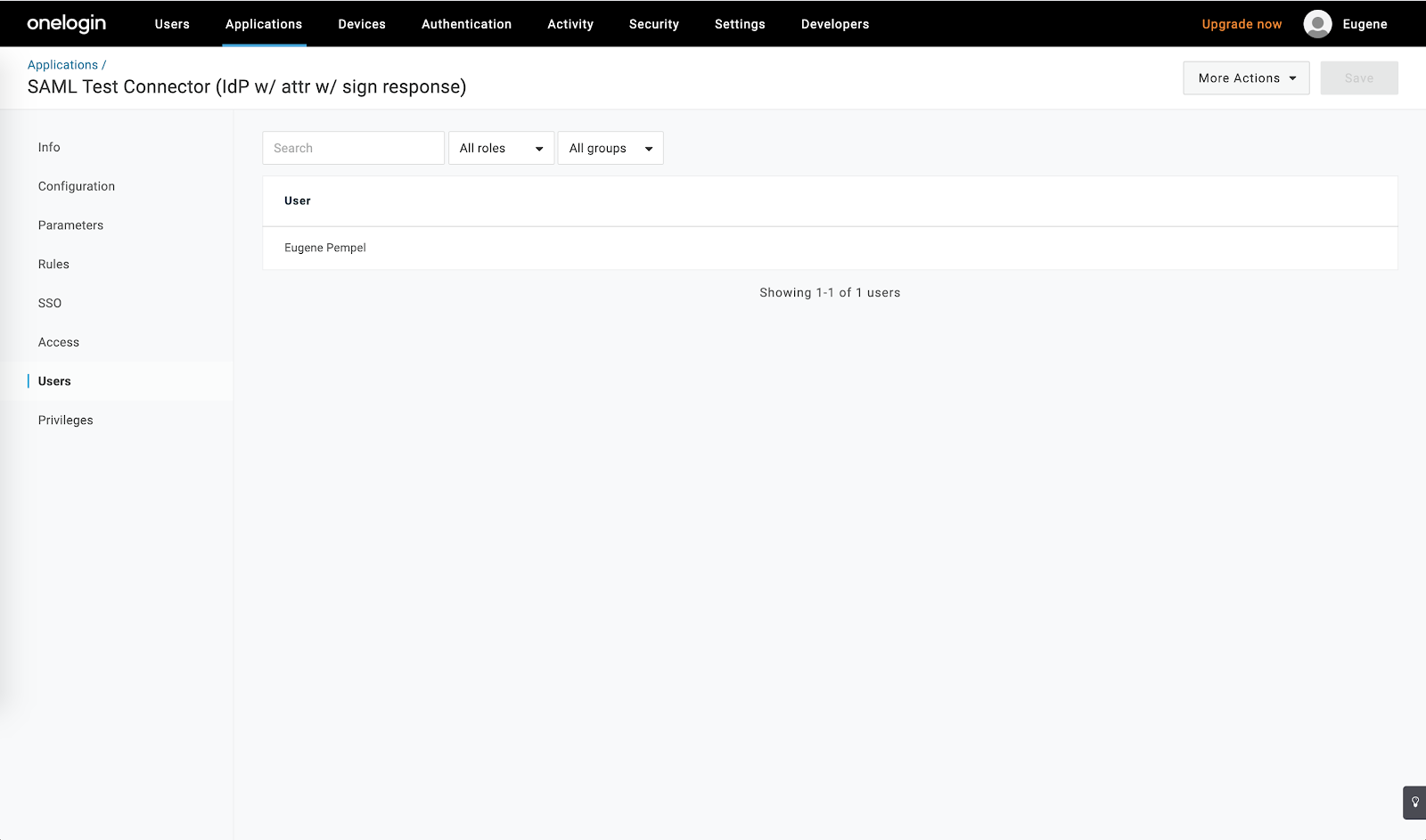
- On the “Users” tab you can see the complete list of users who have access to the newly created OneLogin application:
- Go to the “SSO” tab and change “SAML Signature Algorithm” to “SHA-256”:
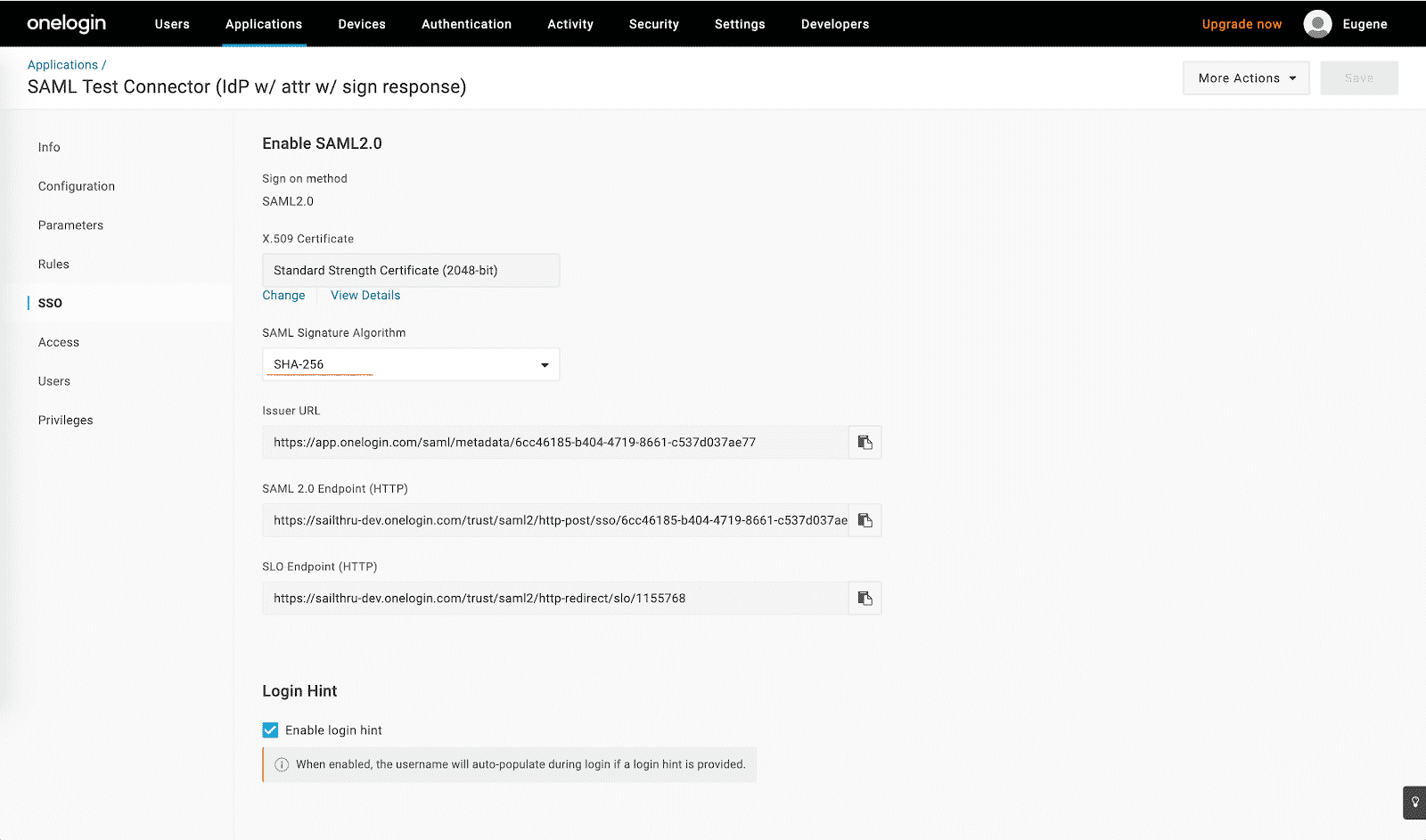
- On the “SSO” tab, download the X.509 certificate. For that click on the “View Details” link at the “X.509 Certificate” field and then download the X.509 certificate “onelogin.pem”.
- On the “SSO” tab, copy the value for “SAML 2.0 Endpoint (HTTP)”.
Pass configuration details to Marigold Engage by Sailthru
Once you have completed all these steps, please contact Support with the following details- SAML connection name
- Identity Provider Single Sign-On URL
- X.509 Certificate